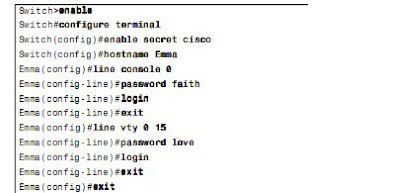
To reach a switch’s enable mode, a user must reach user mode either from the console or
from a Telnet or SSH session, and then use the enable command.
To reach enable mode from a vty (Telnet or SSH), the switch must be configured with
several items:
■ An IP address
■ Login security on the vty lines
■ An enable password
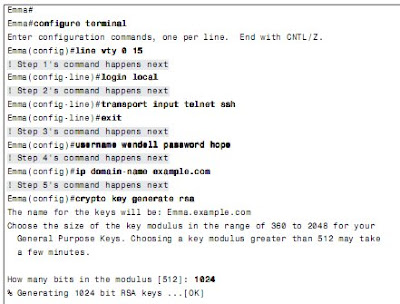
Configuring Usernames and Secure Shell (SSH)
Telnet sends all data, including all passwords entered by the user, as clear text.
SSH encrypts the data sent between the SSH client and the SSH server.
Step 1 Change the vty lines to use usernames, with either locally configured usernames
or an AAA server. "Login" command.
Step 2 Tell the switch to accept both Telnet and SSH with the transport input
telnet ssh vty subcommand. (The default is transport input telnet, omitting the ssh parameter.)
Step 3 Add one or more username name password pass-value global configuration commands to configure username/password pairs.
Step 4 Configure a DNS domain name with the ip domain-name name global configuration command.
Step 5 Configure the switch to generate a matched public and private key pair, as well as a shared encryption key, using the crypto key generate rsa global configuration command.
Step 6 Although no switch commands are required, each SSH client needs a copy of the switch’s public key before the client can connect.
Enable Mode Passwords
■ If the global configuration command enable password actual-password is used, it
defines the password required when using the enable EXEC command. This password
is listed as clear text in the configuration file by default.
■ If the global configuration command enable secret actual-password is used, it defines
the password required when using the enable EXEC command. This password is listed
as a hidden MD5 hash value in the configuration file.
■ If both commands are used, the password set in the enable secret command defines
which password is required.
Password Encryption
■ When the service password-encryption command is configured, all existing console,
vty, and username command passwords are immediately encrypted.
■ If the service password-encryption command has already been configured, any future
changes to these passwords are encrypted.
■ If the no service password-encryption command is used later, the passwords remain
encrypted, until they are changed—at which point they show up in clear text.
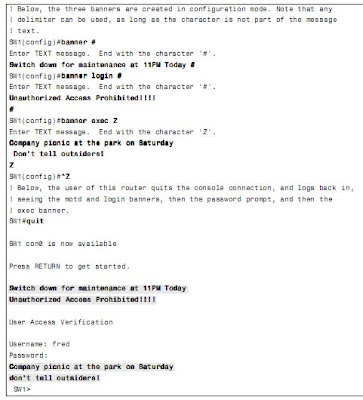
Banners
Cisco routers and switches can display a variety of banners depending on what a router or
switch administrator is doing. A banner is simply some text that appears on the screen
for the user.

Logging synchronous and exec-timeout Commands
To make using the console a little easier, you can tell the switch to display syslog messages
only at more convenient times, such as at the end of output from a show command or to
prevent the interruption of a command text input. To do so, just configure the logging
synchronous console line subcommand.
By default, the switch or router automatically disconnects users after 5 minutes of inactivity, exec-timeout minutes seconds, set the timeout to 0 minutes and 0 seconds, the router never times out the console .
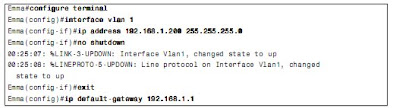
Configuring the Switch IP Address
This interface plays the same role as an Ethernet interface on a PC.
In effect, a switch’s VLAN 1 interface gives the switch an interface into the default VLAN.
Port Security
Use port security to restrict that interface so that only the expected devices can use it.
Reduces exposure to some types of attacks in which the attacker connects a laptop to the wall socket that connects to a switch port that has been configured to use port security
Step 1 Make the switch interface an access interface using the switchport mode access
interface subcommand.
Step 2 Enable port security using the switchport port-security interface subcommand.
Step 3 (Optional) Specify the maximum number of allowed MAC addresses associated with the interface using the switchport port-security maximum number interface subcommand. (Defaults to one MAC address.)
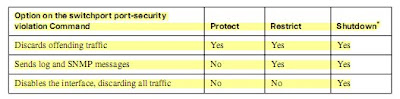
Step 4 (Optional) Define the action to take when a frame is received from a MAC address other than the defined addresses using the switchport port-security violation {protect | restrict | shutdown} interface subcommand. (The default action is to shut down the port.)
Step 5A Specify the MAC address(es) allowed to send frames into this interface using the switchport port-security mac-address mac-address command. Use the command multiple times to define more than one MAC address.
Step 5B Alternatively, instead of Step 5A, use the “sticky learning” process to dynamically learn and configure the MAC addresses of currently connected hosts by configuring the switchport port-security mac-address sticky interface subcommand.
■ Shutdown—The port immediately is put into the errdisable state, which effectively shuts it
down. It must be re-enabled manually or through errdisable recovery to be used again.
■ Restrict—The port is allowed to stay up, but all packets from violating MAC addresses are
dropped. The switch keeps a running count of the number of violating packets and can send
an SNMP trap and a syslog message as an alert of the violation.
■ Protect—The port is allowed to stay up, as in the restrict mode. Although packets from
violating addresses are dropped, no record of the violation is kept.
VLAN Configuration
Cisco switch interfaces are considered to be either access interfaces or trunk interfaces.
Access interfaces send and receive frames only in a single VLAN, called the access VLAN.
Trunking interfaces send and receive traffic in multiple VLANs.
Step 1 To configure a new VLAN:
a. From configuration mode, use the vlan vlan-id global configuration command
to create the VLAN and move the user into VLAN configuration mode.
b. (Optional) Use the name name VLAN subcommand to list a name for the VLAN. If not configured, the VLAN name is VLANZZZZ, where ZZZZ is the four-digit decimal VLAN ID.
Step 2 To configure a VLAN for each access interface:
a. Use the interface command to move into interface configuration mode for each
desired interface.
b. Use the switchport access vlan id-number interface subcommand to specify the VLAN number associated with that interface.
c. (Optional) To disable trunking so that the switch will not dynamically decide to use trunking on the interface, and it will remain an access interface, use the switchport mode access interface subcommand.
Securing Unused Switch Interfaces
The recommendations for unused interfaces are as follows:
■ Administratively disable the interface using the shutdown interface subcommand.
■ Prevent VLAN trunking and VTP by making the port a nontrunking interface using the
switchport mode access interface subcommand.
■ Assign the port to an unused VLAN using the switchport access vlan number
interface subcommand.
No comments:
Post a Comment